30+ threat model data flow diagram
The first option opens the File Open screen. Threat modeling uses traditional Data Flow Diagrams DFDs 8 with security-speciflc annotations to describe how data enters leaves and traverses the system.

Flowchart Symbols Flow Arrows Programming Process Flow Chart Symbols Chart
Use Lucidchart to visualize ideas make charts diagrams more.
. Visual Paradigm Online features an online threat model maker and a large variety of technical and. By Laurens Sion and colleagues. Create threat models online.
One large project at. The analysis uses a Data Flow Diagram DFD to describe how data. Swim Lane Diagrams Swim lane diagrams are a common way to represent.
Data flows and trust boundaries can be added to the diagram by clicking their shape in the stencil on the left side of the diagram editor. Threat modeling analyzes how an adversary might attack a system by supplying it with malicious data or interacting with it. This white paper looks at some flaws and the advantages of moving to a more mature Process Flow Diagram PFD approach to threat modeling as a solution.
The data flow diagram will outline the point at which the data will have to cross from the IoT device into the network allowing the team to set up a trust boundary at this location. Are Data Flow Diagrams Enough. In this step Data Flow Diagram should be divided in the context of Model View Controller MVC.
In this longest episode of the worlds shortest threat modeling videos I introduce the five. Once added their ends can be dragged around the. Ad Get the most powerful professional diagram software on the market.
This information is documented in a resulting Threat Model document. Ad Get the most powerful professional diagram software on the market. Data flow diagrams are very frequently used in threat modeling.
This weeks threat model Thursday looks at an academic paper Security Threat Modeling. Some of the most valuable key. It is also used to produce data flow diagrams DFDs for the application.
Save Time by Using Our Premade Template Instead of Creating Your Own from Scratch. A threat model diagram is a visual form of threat model. Open a model Hover over Open A Model to reveal two options.
Use tools to draw your diagram If you dont like to manually draw your DFD. Use Lucidchart to visualize ideas make charts diagrams more. Use a data flow threat model analysis with the aid of intelligence tools to determine additional areas that are outside the boundary of common knowledge.
The DFDs show the different paths through the. Open From This Computer and Open From OneDrive. Ad Develop a Step-by-Step Visual Guide to Different Processes.
UML to add trust boundaries to those diagrams than to create new diagrams just for threat modeling.

Threat Modeling Demystified

Threat Modeling Demystified
What S The Difference Between A Data Flow Diagram And Use Case Diagram In Terms Of Construction And Usage Quora
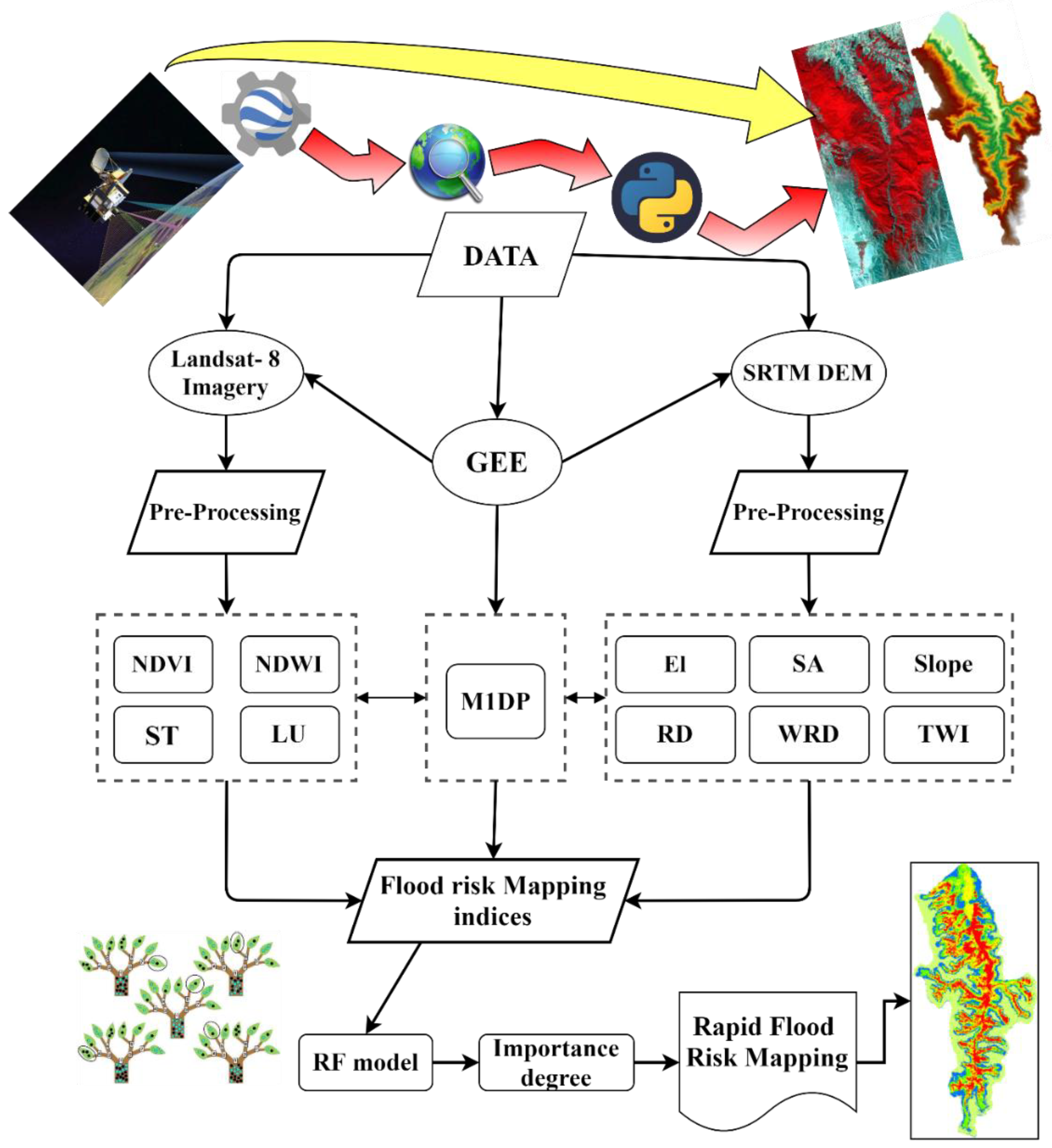
Water Free Full Text Flood Risk Mapping By Remote Sensing Data And Random Forest Technique Html
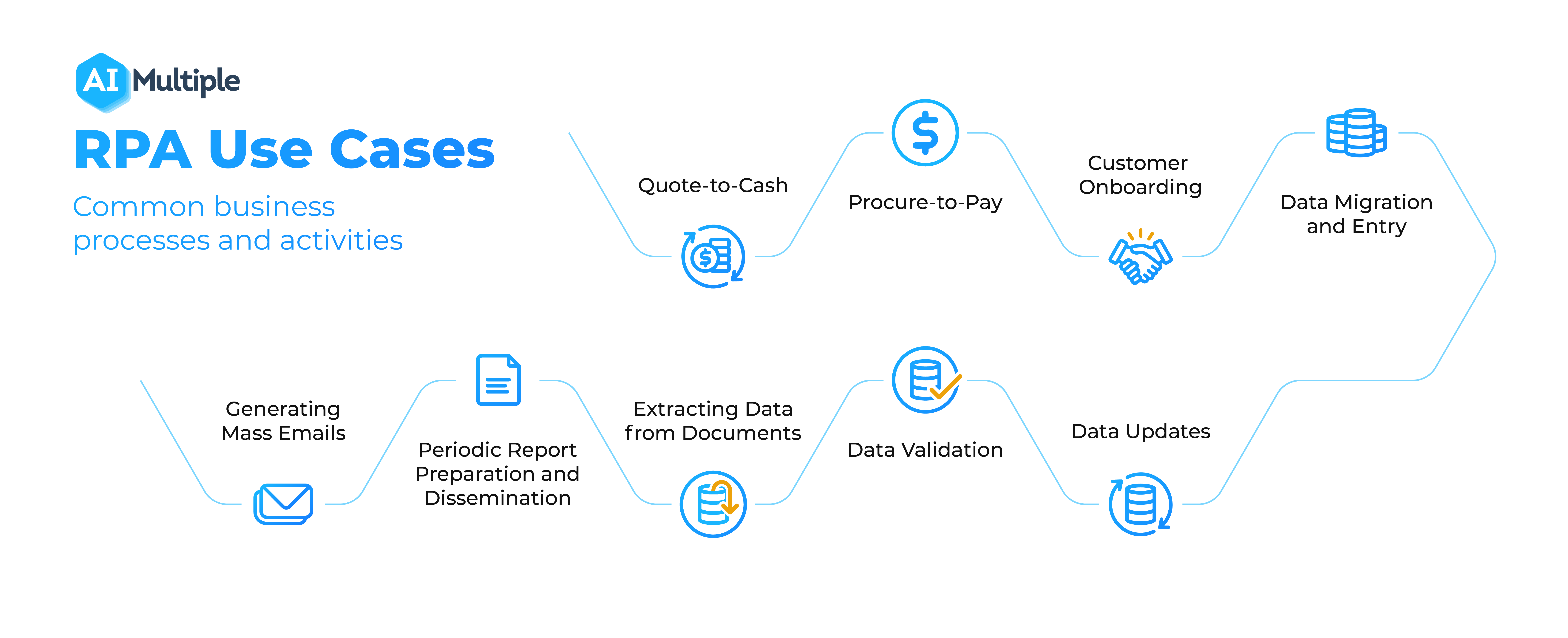
Top 68 Rpa Use Cases Projects Applications Examples In 2022

Project Evaluation And Review Technique Activity On Arrow Diagram Design Network Engineer Diagram
How To Simplify A Complex And Frustrating Change Management Process When Delivering Software To Production Quora

Threat Modeling Demystified
1

Graphing The Utility Grid On Aws Aws For Industries

Threat Modeling Demystified
What Is The Relationship Between A Context Diagram And Diagram 0 Quora

Threat Modeling Demystified
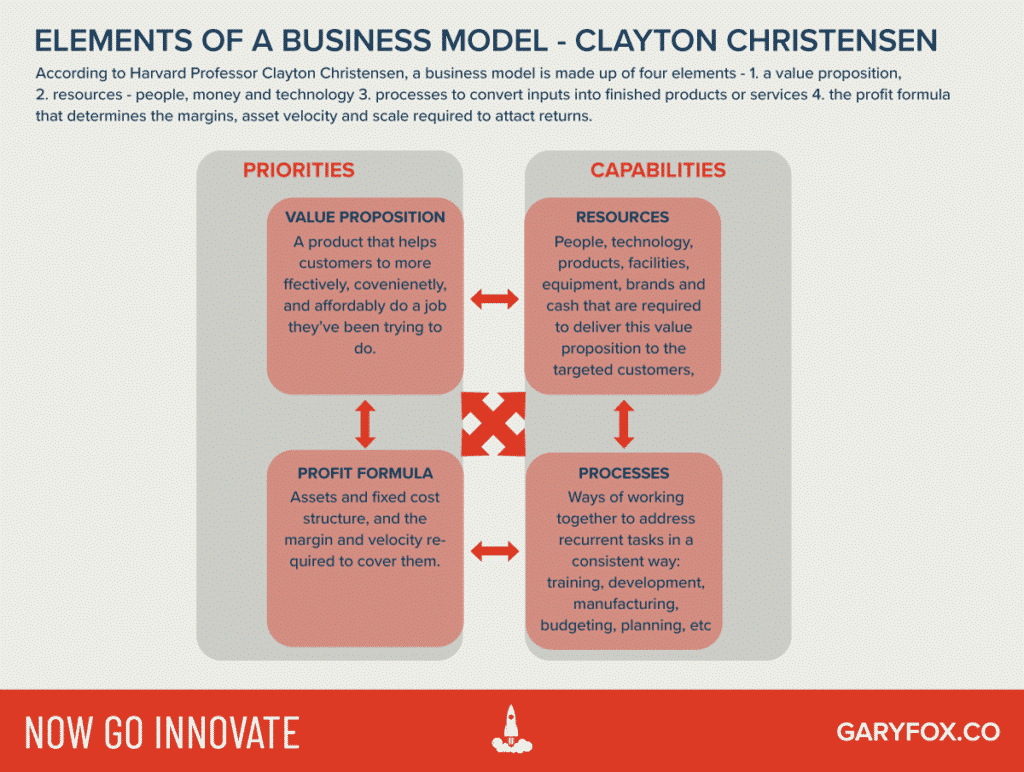
What Is A Business Model Definition Explanation 30 Examples
1
What Is The Purpose Of Developing Dfds Quora
![]()
Threatmodeler About The Evolution Of Threat Modeling